would you like to make your network more resilient from attackers to stop attacks like ransomware or to stop attackers from pivoting from one machine to another and exfiltrating confidential data from your organization then you need to look into how can network segmentation protect cardholder data and your organization by implementing through best practices
In this article will find How Network Segmentation Decreases Both Performance and Security on a Network and how can we help small and mid-sized organizations improve their defenses and reduce the risk of breaches before we dig into the deep.
let’s be sure we define what is network segmentation and the advantages of network segmentation by dividing a computer network into smaller zones to reduce the amount of communication between devices.
Network Segmentation Diagram
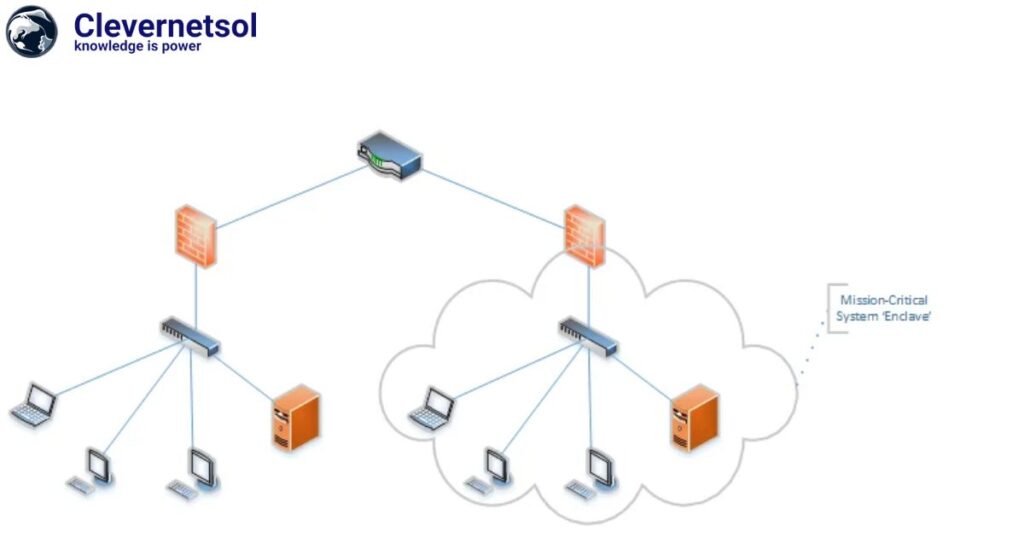
this can be done both physically and virtual network segmentation which reducing congestion on your network for improving performance as well as for enhancing security which is what we are focused on.
on this channel there’s no reason that every device on your network should be able to communicate yes
Devices need to communicate your computer, needs to be able to talk to your printer and your computer needs to be able to talk to your file server.
But many organizations have devices on their networks that really don’t need to communicate it is best to segmenting a network logically
Network segmentation Security Best Practices
Network segmentation best practices begin separating these devices out from one another and if you think about the way a network is structured it actually is sort of segmented by default.
we just don’t realize it an ip range a standard /24network with a 255. 255.subnet can only have 254 devices on the network
so, the first reason that we mentioned that macro segmentation network is good for traffic congestion
How to Segment Your Network
If you think about a broadcast message as an example. when a device is looking for another device it sends out a broadcast message to every device on that segment and every device that receives the message has to read it process it ignore it or respond now.
imagine 200 devices or 250 devices and all sending out broadcast message and your devices are being bombarded with this all the time and implementing segmentation instead of 250 devices
what if we bring that down and we only have maybe 16 devices in this segment?
Now it only has to respond to 16 broadcast messages or broadcast messages from 16 devices we have greatly reduced the congestion and the workload.
for these devices on our network so there are typically two ways that an organization would go about beginning to segment a network physically and virtually.
Physical segmentation is just what it sounds like we physically separate the network via switches and routers we then join those two together so they can communicate.
you could see an example of this with an organization with multiple location and such location has its own network at the edge they have a router and those routers communicate with each other while this is definitely a very effective way and a very sure way to segment a network.
It would be very expensive if you try to implement segmentation physically within your environment
so, another option for segmentation is virtual segmentation and in virtual Network segmentation we are usually talking about vlans or virtual local area networks and this is done with vlan tagging.
so, a special tag is modified on all of the packets on your network to identify which vlan those packets belong to then at the switch level.
Each switch is configured on certain ports to only allow communication from certain VLANs so you might have a router and a couple of switches and each switch might have two VLANs on them and each port would then have tags specifying which VLANs they’re allowed to communicate with then when traffic comes to those ports.
if they are not specified for that VLAN those packets coming in they are ignored and this is the method we typically see in today’s networks.
we usually see VLAN implementation however VLANs on their own can be bypassed it is not very hard for an attacker to do what is called a VLAN hopping attack and cross these VLAN bridges
so, for security purposes, the best way to do this is to route your VLANs through a next-generation firewall and this is the approach we take in Zero trust each VLAN is routed through a next-generation firewall and that traffic is inspected.
so, when you design VLANs there are a few common VLANs you might have and the demilitarized zone which is typically a subnet or a segment that is used for containing services that communicate with the internet.
servers like web servers, FTP servers, and in your router those types of devices might go in a VLAN that is a de motorized zone.
next, you should have your guest wireless networks if you have a guest wi-fi or you have wi-fi for your employees to connect their smartphones and personal devices to that should be segmented as well.
There is a security risk if these individuals connect your network if they have infected devices or if they try to perform malicious activities on your network.
so, segmenting them to a guest network or a guest wireless network is a smart move its management.
Another segment to consider it administrators because we have to use administrative access and many times, they’re operating using administrative credentials.
Administrative credentials have much more access than an ordinary user and because of this they are targets of attackers and segmenting them into their own administrative network is another smart move.
VoIP networks should typically be separated as well into their own segment
VoIP traffic can be sensitive to interference or to congestion and there are controls such as quality of service that you can implement but another problem that we see with networks a lot of times.
when we audit VoIP technology many times, we found the devices and phones are older and if an organization has something like network access control in place, they may have robust network access control in place but the VoIP phones don’t support it
So, a lot of times the ports that they are connected to the segments they communicate on have fewer restrictions than others and a lot of times as an attacker can use those ports to gain access into your network.
so, segmenting those out is another good security strategy.
The final segment that I’d like to suggest is one for industrial networks
if your organization is a manufacturing organization then you should consider segmenting your industrial networks.
There are your robots CNC machines any devices that have to do with your industrial systems many times are running outdated operating systems embedded operating systems that have lots of vulnerabilities and they are a huge risk to your organization they could become pivot points for an attacker.
If they could compromise these and begin a ransomware infection throughout your network especially if they’re joined to your domain like we mentioned at the beginning there are definitely security benefits from network segmentation as an attacker.
when we perform PCI network segmentation testing on networks that have proper segmentation in place really makes it hard for us to pivot to increase our foothold to move to other machines.
what is the disadvantage of having a flat network design
A flat network or a network where all the devices are on the same subnet or the same segment it is very easy for an attacker to compromise one system pivot to another pop to another.
When you adding segmentation creates roadblocks for the attacker it makes it harder and longer and it gives you a better chance to find them in your network
so, network segmentation is a must-do for every organization pretty much every organization has items on their network that should be segmented from each other it is the control you should put in place.
